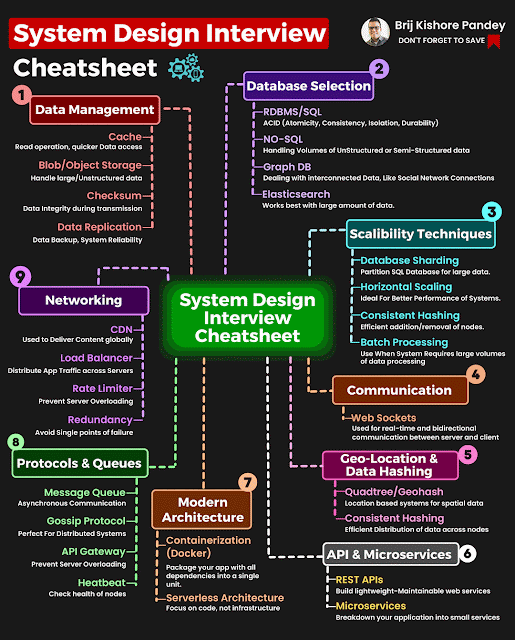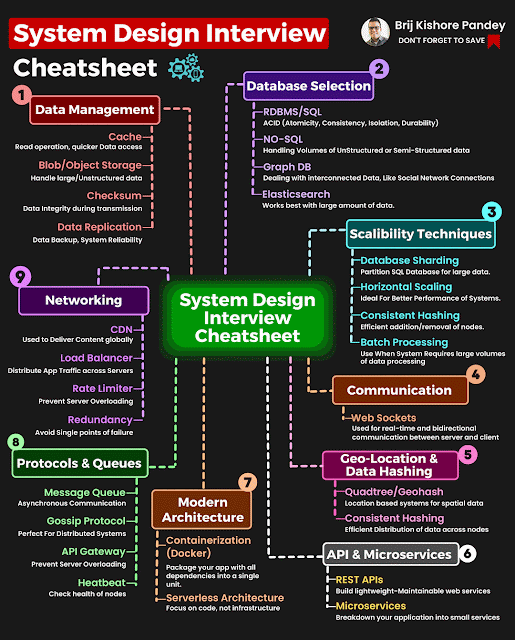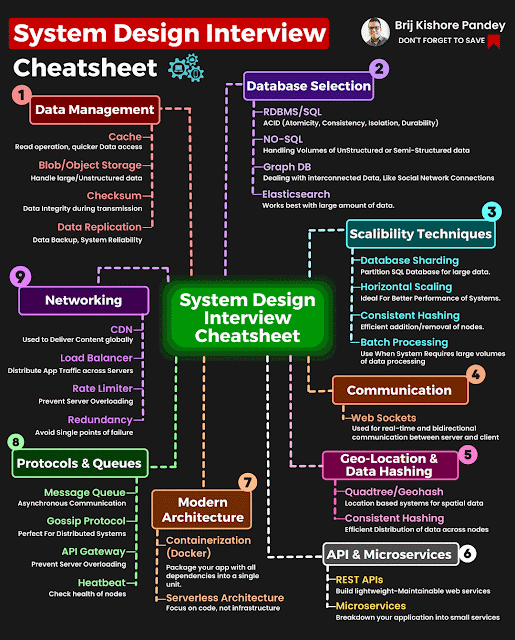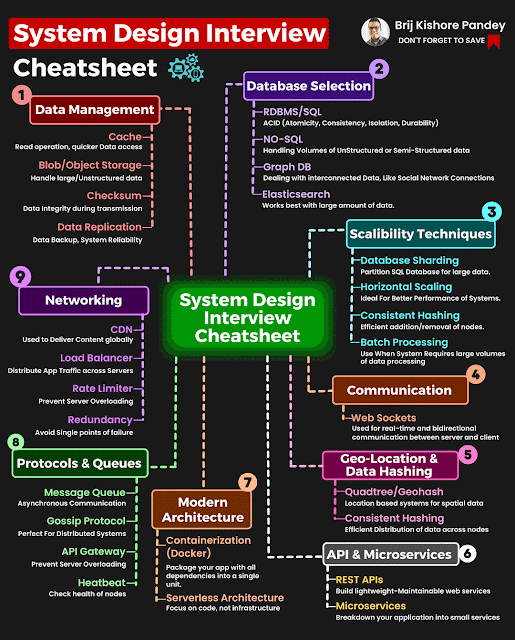
How To Install OpenVAS Using Docker in few Minutes
OpenVAS The Open Vulnerability Assessment System, OpenVAS is a comprehensive open-source vulnerability scanning tool and vulnerability management system. It's free of cost, and its components are free software, most licensed under the GNU GPL. let's update our repository apt-get upgrade -y install docker if you don't have one. apt install docker.io lets run the docker and parallelly install openvas . docker run -d -p 443:443 --name openvas sami/openvas Let's verify the installation by visiting the local address. Thanks for reading out my article. Please visit again for updates.